Client-Server vs Peer-to-Peer Networks Explained
Lesson 8: Client–Server vs Peer-to-Peer Networks
Intent:
To compare centralized (client–server) and decentralized (peer-to-peer) network architectures, and explain how peer discovery and data propagation work in blockchain systems.
Introduction – How Computers Talk to Each Other
Behind every website, app, or blockchain lies a network architecture – the way computers communicate, share data, and coordinate actions.
Most of today’s internet runs on client-server networks, where a central server controls communication.
Blockchain, however, depends on a very different model: peer-to-peer (P2P) networking.
In this lesson, we’ll compare these two architectures, explain how peers find each other, and explore how data spreads across decentralized networks – all without a central coordinator.
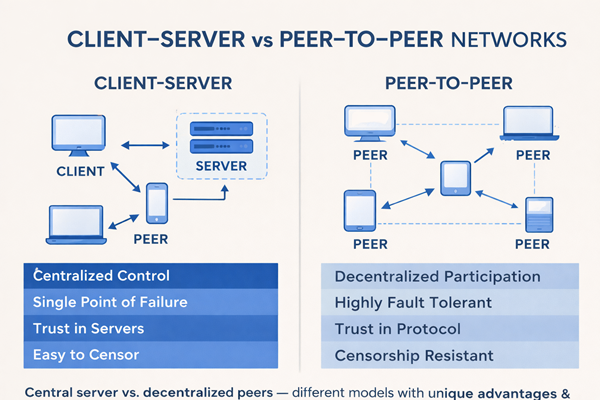
What Is a Client Server Network?
In a client-server architecture, communication flows through a central server.
- Clients request data or services
- Servers store data, process logic, and send responses
Examples you use every day:
- Websites (browser → web server)
- Banking apps (mobile app → bank server)
- Social media platforms (user → platform servers)
How It Works (Simple Flow):
Client → Server → Client
The server decides:
- Who can access data
- What data is returned
- When requests are accepted or denied
This model is efficient, fast, and easy to manage – but it creates central points of control and failure.
Limitations of Client–Server Systems
While widely used, client–server networks come with trade-offs:
- Single Point of Failure: If the server goes down, the service stops.
- Censorship & Control: The server owner can block users or modify data.
- Scalability Costs: Scaling requires expensive infrastructure.
- Trust Dependency: Users must trust the server to behave honestly.
These limitations become critical when building open, global, trust-minimized systems – which is where peer-to-peer networks come in.
What Is a Peer to Peer (P2P) Network?
In a peer-to-peer network, all participants are equals – called peers.
- Each peer can send, receive, and verify data
- No central server controls the network
- Data is shared directly between peers
How It Works (Simple Flow):
Peer ↔ Peer ↔ Peer ↔ Peer
Blockchain networks like Bitcoin and Ethereum rely on P2P architecture to stay decentralized, censorship-resistant, and resilient.
Why Blockchain Uses Peer-to-Peer Networks
Blockchains require:
- No single authority
- Shared state across thousands of nodes
- Resistance to outages and censorship
A P2P network enables:
- Decentralized validation of transactions
- Redundancy – many copies of the ledger exist
- Fault tolerance – some nodes can fail without breaking the system
In short, decentralization starts at the network layer.
Peer Discovery – How Nodes Find Each Other
Unlike client-server systems, P2P networks don’t have a fixed directory.
So how do peers find one another?
Common peer discovery methods include:
- Bootstrapping Nodes
New nodes start with a small list of known peers (hardcoded or DNS-based). - Peer Exchange (PEX)
Connected peers share information about other peers they know. - Distributed Hash Tables (DHTs)
A decentralized lookup system where peers help locate other peers.
Once connected, nodes maintain a peer list and constantly refresh it.
Data Propagation – How Information Spreads
When a transaction or block is created, it must reach the entire network.
This happens through gossip-based propagation.
Step-by-Step Propagation:
- A peer receives new data (transaction or block)
- It verifies the data locally
- It forwards the data to its connected peers
- Those peers repeat the process
Like word-of-mouth news, data spreads rapidly without central broadcasting.
This ensures:
- Fast distribution
- Redundancy
- Resistance to censorship
Client–Server vs Peer-to-Peer – Side-by-Side Comparison
| Feature | Client–Server | Peer-to-Peer |
|---|---|---|
| Control | Centralized | Decentralized |
| Failure Risk | Single point of failure | Highly fault tolerant |
| Scalability | Infrastructure-heavy | Network grows organically |
| Trust Model | Trust the server | Trust the protocol |
| Censorship Resistance | Low | High |
| Example | Websites, banks | Blockchain, BitTorrent |
Each architecture has valid use cases – blockchain simply requires P2P by design.
Real-World Analogy
- Client–Server: A classroom where students must ask the teacher for all information.
- Peer-to-Peer: A study group where everyone shares notes directly with each other.
The second scales better – and no single person controls the conversation.
Challenges of Peer-to-Peer Networks
P2P networks aren’t perfect. They introduce new challenges:
- Latency: Data takes time to reach all peers.
- Network Overhead: Duplicate messages increase traffic.
- Sybil Attacks: Fake nodes attempt to influence the network.
- Coordination Complexity: No central authority to enforce rules.
Blockchain protocols address these issues through consensus, cryptography, and incentives.
Why P2P Networks Enable Trustless Systems
By removing central servers:
- No one can secretly alter history
- No single outage can stop the network
- Participants verify data independently
This makes P2P networks ideal for financial systems, identity, and global coordination — where trust must be minimized.
Key Takeaway
Client–server networks optimize for speed and control.
Peer-to-peer networks optimize for resilience, openness, and decentralization.
Blockchain chooses P2P not because it’s easier –
but because trustless systems require trustless networking.
Next Lesson Preview
👉 Lesson 9: Consensus Basics – How the Network Agrees on Truth
We’ll explore how decentralized peers reach agreement without a leader – and why consensus is the backbone of blockchain security.