Identity & Signatures – Verifying Senders in Blockchain
Lesson 11: Identity & Signatures – Verifying Senders
Intent:
To explain how cryptographic keys and digital signatures verify identity, prove ownership of assets, and prevent fraud in blockchain systems.
Introduction – Who Is Really Sending the Transaction?
In traditional systems, identity is verified through:
- Usernames
- Passwords
- Banks or centralized authorities
Blockchain works differently.
There are no accounts, no logins, and no central identity provider.
Yet, the network can still prove who owns what and who authorized a transaction – without ever knowing a person’s real-world identity.
This is made possible through cryptographic keys and digital signatures.
Identity in Blockchain – No Names, Only Keys
Blockchain identity is pseudonymous.
Instead of names or emails, users are represented by:
- Public keys (or addresses)
- Private keys (secret)
Your identity = your cryptographic keys
Control of the private key equals control of the funds.
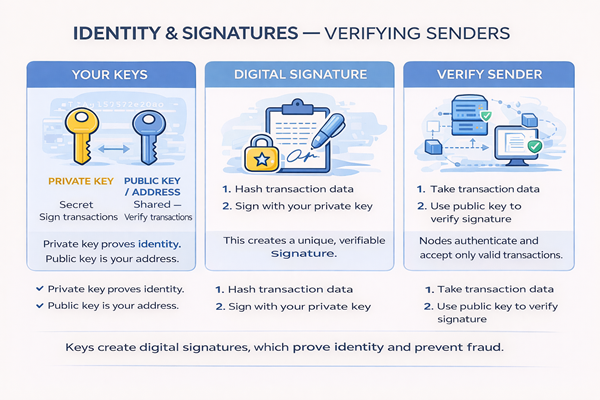
Public Keys vs Private Keys
Each blockchain user has a key pair:
Private Key
- Secret
- Used to sign transactions
- Must never be shared
- Proves ownership
Public Key / Address
- Shared openly
- Used to verify signatures
- Receives funds
- Derives the blockchain address
Anyone can see addresses – but only the private key holder can authorize spending.
What Is a Digital Signature?
A digital signature is a cryptographic proof that:
- The sender owns the private key
- The transaction hasn’t been altered
- The sender explicitly approved the transaction
It’s created by:
- Hashing the transaction data
- Signing the hash with the sender’s private key
This signature is included in the transaction and broadcast to the network.
How Signature Verification Works
When a node receives a transaction, it:
- Takes the transaction data
- Uses the sender’s public key
- Verifies the signature mathematically
If the signature is valid:
- The sender is authenticated
- The transaction is accepted
If invalid:
- The transaction is rejected instantly
No identity authority is required – math does the verification.
Why Signatures Prevent Fraud
Digital signatures protect against:
- Forged transactions
- Impersonation
- Data manipulation
- Unauthorized spending
Even if an attacker sees:
- Your public address
- Your transaction history
They cannot create a valid signature without your private key.
Ownership in Blockchain – Spend Authorization
Blockchain doesn’t track “accounts” in the traditional sense.
Instead, it tracks:
- Which public keys can spend which outputs (UTXO model)
- Or which addresses control balances (account-based model)
In both cases:
Ownership = ability to produce a valid signature
This is why “not your keys, not your coins” is a fundamental rule.
Real-World Analogy – Handwritten vs Digital Signatures
- A handwritten signature can be forged
- A digital signature cannot (without the private key)
Digital signatures are:
- Unique
- Verifiable
- Tamper-proof
- Non-repudiable
Once signed, a transaction cannot be denied or altered.
Common Signature Algorithms in Blockchain
| Algorithm | Used By | Purpose |
|---|---|---|
| ECDSA | Bitcoin | Transaction signing |
| EdDSA | Solana, others | Faster, modern signing |
| Schnorr | Bitcoin (Taproot) | Aggregated signatures |
All serve the same goal – secure ownership proof.
What Happens If You Lose Your Private Key?
- No recovery option
- No password reset
- No customer support
The blockchain will still recognize the address – but no one can authorize spending.
This is the trade-off for full self-sovereignty.
Privacy vs Identity
Blockchain identities are:
- Pseudonymous, not anonymous
- Transparent in activity
- Private in real-world identity
Users control when and how identity is revealed – not the network.
Why Identity & Signatures Matter
Without cryptographic signatures:
- Anyone could spend anyone else’s funds
- Fraud would be trivial
- Trustless systems would fail
Signatures allow blockchain to be:
- Permissionless
- Secure
- Self-sovereign
Key Takeaway
Blockchain identity isn’t about who you are —
it’s about what you can prove.
Cryptographic keys and digital signatures:
- Replace trust with math
- Replace identity providers with ownership proofs
- Make fraud computationally impossible
Control your keys – and you control your assets.
Next Lesson Preview
👉 Lesson 12: Wallets Explained – Hot, Cold & Smart Contract Wallets
We’ll explore how keys are stored, protected, and used in different wallet designs.