The Block – How Data Becomes Tamper-Proof
Intent: (The Block – How Data Becomes Tamper-Proof) Explain how blockchain packages data into secure “blocks” and ensures immutability through cryptography.
Introduction – Building Blocks of Digital Trust
Imagine a digital notebook where every page is permanently sealed once it’s filled – no erasing, no rewriting, just adding new pages. That’s exactly how blockchain works.
Every blockchain — whether Bitcoin, Ethereum, or a supply chain ledger – relies on a simple but powerful idea: data stored inside “blocks” that are cryptographically linked together.
In this lesson, we’ll explore how data becomes tamper-proof, what’s actually inside a block, and why this structure guarantees integrity and trust without a central authority.
What Is a Block?
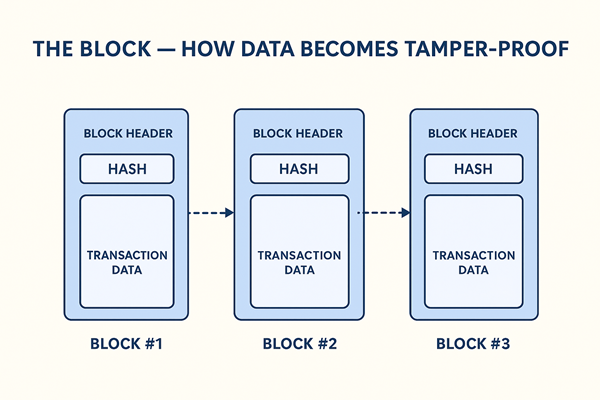
A block is a digital container – a bundle of transactions or data grouped together.
Each block has three main components:
- Block Header: Metadata about the block (timestamp, version, and reference to the previous block).
- Transaction Data: The actual records being added – payments, contract actions, or other information.
- Hash: A unique digital fingerprint representing all the data inside the block.
Think of it like sealing a box: the items inside (transactions) can’t be changed without breaking the seal (the hash).
How Hashing Makes Data Tamper-Proof
A hash function converts any data — no matter how large — into a fixed-length string of characters.
Example:
- Input: “Hello World” → Output:
a591a6d40bf420404a011733cfb7b190... - Even a single comma change produces a completely different hash.
This means:
- Each block’s hash depends on its data.
- If anyone tries to alter even one transaction, the hash changes instantly — alerting the entire network.
Hashes act as digital DNA — they prove the block’s data hasn’t been altered since it was created.
How Blocks Link Together – The Chain Effect
Here’s where the genius lies: each block contains the hash of the previous block.
This creates a continuous, chronological chain.
If you change Block #25, its hash changes — and that breaks the link to Block #26.
To cover your tracks, you’d have to recalculate every block after #25 — an almost impossible task on large blockchains.
That’s why blockchain data is considered immutable — once added, it’s there forever, visible and verifiable.
Proof of Work: Securing the Block Creation Process
In many blockchains (like Bitcoin), adding a block isn’t just about appending data — it’s about earning the right to do so.
Here’s how Proof of Work (PoW) ensures fairness and security:
- Miners compete to solve a complex mathematical puzzle based on the block’s data.
- The first to solve it broadcasts the solution.
- Other nodes verify the solution quickly, ensuring it’s valid.
- The winning miner adds the block to the chain and earns a reward.
This process requires massive computing effort — meaning to tamper with data, an attacker would need to redo all that work and outpace the rest of the network.
Alternative: Proof of Stake (PoS)
Modern blockchains use Proof of Stake, where validators are chosen based on how much cryptocurrency they “stake” (lock up as collateral).
It’s faster and more energy-efficient than Proof of Work — but the principle remains the same:
- Validators who act honestly are rewarded.
- Those who cheat risk losing their stake.
Why This Structure Works – Mathematical Integrity
Let’s summarize why blockchain data stays tamper-proof:
- Every block’s hash depends on its content.
- Each block references the previous one’s hash.
- Any change breaks the chain, and the network rejects it.
- Consensus mechanisms prevent unauthorized blocks from being accepted.
So instead of a single authority verifying records, mathematics and majority consensus guarantee their integrity.
Real-World Analogy – The Sealed Ledger Book
Imagine an accountant’s ledger where each page is numbered and stamped with a seal that includes the previous page’s number.
If you try to remove or replace one page, every seal after it breaks — and anyone inspecting the book can instantly see it’s been tampered with.
That’s exactly what blockchain does — but digitally, at scale, and globally.
Applications of Tamper-Proof Data
Because blockchain ensures data can’t be secretly modified, it’s ideal for industries where trust and verification are critical:
- Finance: Immutable records of transactions (no double-spending).
- Supply Chains: Tracking goods from source to shelf with verified timestamps.
- Healthcare: Secure, auditable medical record logs.
- Voting: Transparent, verifiable ballots that can’t be altered after submission.
Every one of these use cases relies on the core principle: the block makes data tamper-proof.
Challenges – Not All Chains Are Perfect
While blockchain’s security model is robust, it’s not flawless.
- Scalability: As the chain grows, verifying every block takes more time and storage.
- Energy Costs: Proof of Work consumes significant power.
- Data Permanence: Once data is added — even incorrect or private info — it can’t easily be removed.
That’s why newer protocols and hybrid models focus on layered architectures, where immutable records coexist with flexible off-chain systems.
Conclusion – The Building Block of Trust
Each block in a blockchain is more than just data — it’s a promise that the information within it hasn’t been altered, hidden, or lost.
Through cryptography, consensus, and transparency, blockchains eliminate the need for trust between strangers.
You don’t have to believe in the people — you believe in the math.
In the next lesson, we’ll explore “The Chain – Linking Blocks Together for Trust”, where we’ll see how distributed networks keep this structure synchronized across the globe.



